When starting a PoC or new VDI deployment, in terms of group policy, I want to isolate the new environment as much as possible. I don’t want any existing user and computer settings applying. Often, the project will involve optimization in this area (in this case the introduction of User Management products such as Citrix WEM or VMware UPM).
I will block policy at the VDI OU level and create a loopback policy (REPLACE) so only settings from one place are applying. I may well have to tackle enforced policy here too.
However, this does not take login scripts defined in a users’ AD profile into account. I find that a lot of people are still using this method to map drives, deploy printers, etc. This is pretty old school now and in almost all cases I want to port these settings into UEM/WEM or at a push Group Policy Preferences. But, my focus is primarily on VDI so I do not want to break anything else in the environment, some of these logon scripts have years of service behind them and can be quite complex.
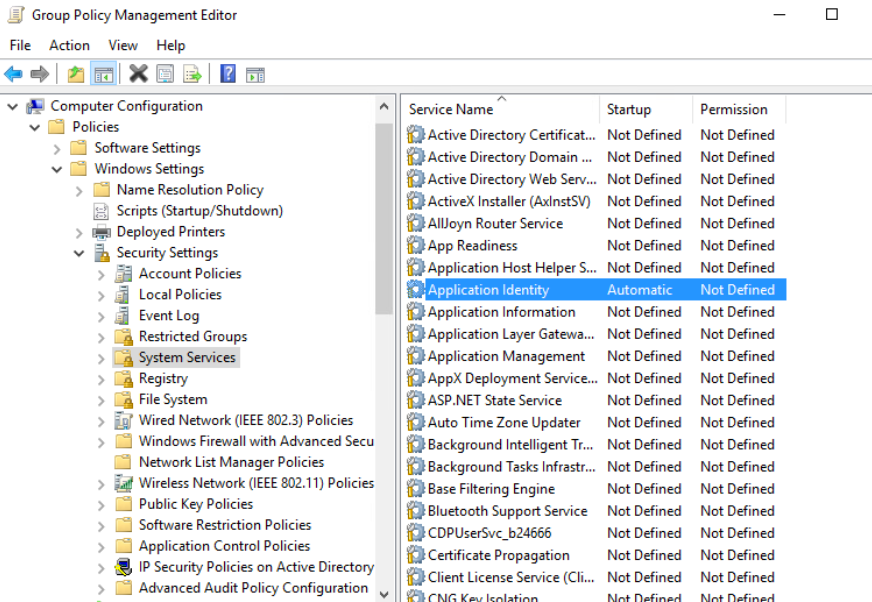
One way around this is to use Applocker rules to block the running of scripts in the VDI OU. Create the default script rules and ensure that the Application Identity service is running on the target desktops. This will catch all AD defined login scripts.
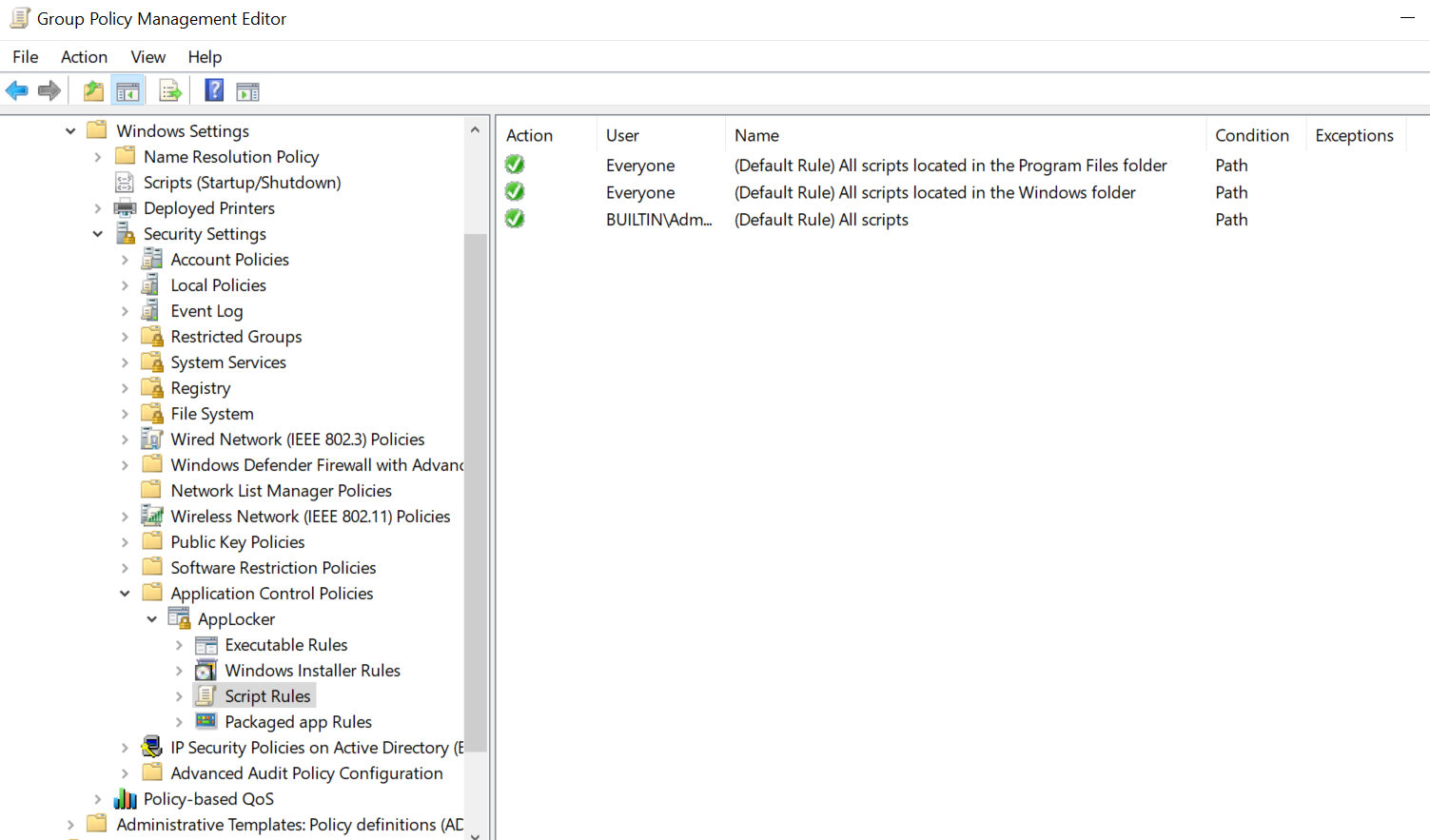
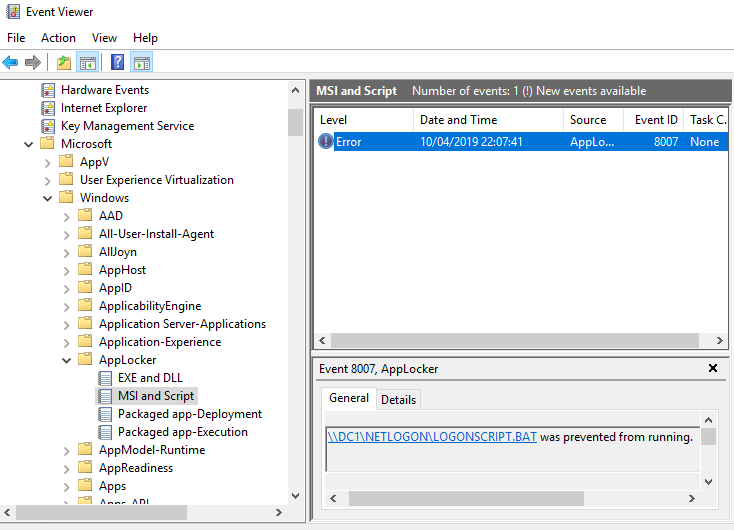
Exceptions can also be added so I would normally add an area of Netlogon that scripts can be run from if required. For troubleshooting, the event log is the place to go (AppLocker events are recorded here).
At this point, I am free to start making decisions about how I am going to deliver configuration settings and test introducing them into the environment.