As part of a security hardening exercise or indeed just because, it may be desirable to change the root account of your ESXi hosts to a complex password, bung it in a safe and let you admins connect via their AD credentials.
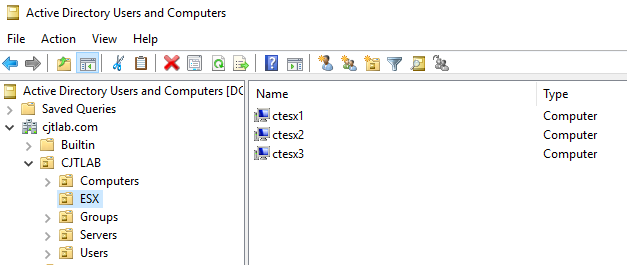
To start with, join your ESXi hosts to your AD domain. I have pre-created computer objects in my test environment.
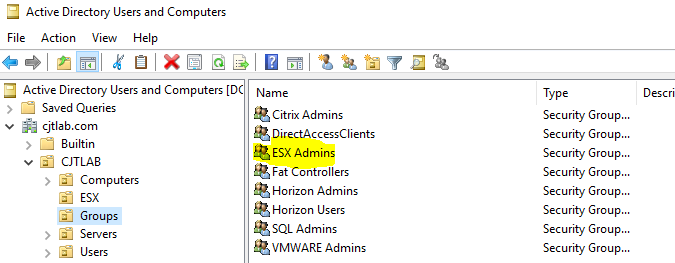
I have also created an ESX Admins AD security group which by default allows its members admin access to an ESXi host once it has been joined to the domain.
To join the domain run the following powercli on your hosts.
$VC = "<Your VCenter>" #vCenter Server
$Domain = "<Your Domain>" #AD Domain
$ESX = "<Your Host>" #ESX Host
Connect-VIServer $VC
#Join Hosts to Domain
Get-VMHost | Get-VMHostAuthentication | Set-VMHostAuthentication -JoinDomain -Domain $Domain
#Check Host Domain Membership
Get-VMhost $ESX | Get-VMHostAuthentication
#Check Admin Group
Get-VMHost $ESX | Get-AdvancedSetting -Name Config.HostAgent.plugins.hostsvc.esxAdminsGroup
If that has worked OK you should get a similar output from my example below.
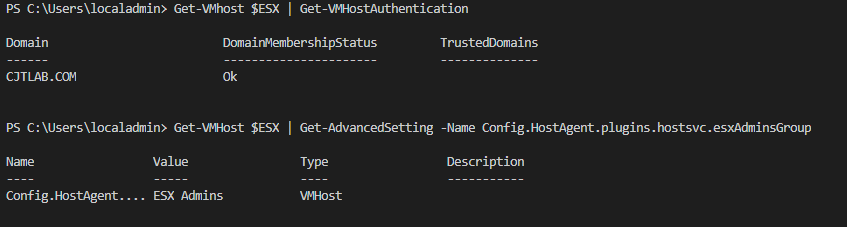
Now in a lab environment, this is fine but we are probably going to want to change that ESX Admins group, the eagle-eyed amongst you would have noticed earlier that I had a “fat controllers” AD group so I am going to use that.
Use the below powercli to change the admin group and start SSH on the host to test logon.
#Change Admin Group
Get-VMHost $ESX | Get-AdvancedSetting -Name Config.HostAgent.plugins.hostsvc.esxAdminsGroup | Set-AdvancedSetting -Value "Fat Controllers"
#Start SSH
Get-VMHost $ESX | Get-VMHostService | Where-object { $_.Key -eq "TSM-SSH" } | Start-VMHostService
Now empty and remove the ESX admins group in AD and try to logon to the host via SSH with AD credentials and it will fail. Add the user to the new AD group specified in the previous step and access is granted. The quick video below demonstrates this.
Remember to disable SSH on the host once you are finished testing.
#Stop SSH
Get-VMHost $ESX | Get-VMHostService | Where-object { $_.Key -eq "TSM-SSH" } | Stop-VMHostService
Hopefully, this has been of some use. One of the things that I am currently looking at is the security hardening of vsphere environments so will more than likely be adding a few more posts around this.